Photo: Andy Wolber / TechRepublic
Google’s email filters usually protect people from problematic email content, such as spam, malicious attachments, and phishing attempts. For example, a message with a virus-infected attachment will likely be blocked by G Suite’s filters, and the system will identify most junk emails and place them in the spam folder.
However, on rare occasions, a phishing message may slip through; or, more accurately, the system will deliver a message to a person’s account and then later identify the email as a phishing attempt. Once identified, G Suite removes the message from the account and notifies a G Suite administrator.
If you’re a G Suite administrator, here are a few things you can do to review and secure accounts once you’re notified that Gmail has detected the delivery of a phishing email.
SEE: Phishing attacks: A guide for IT pros (free PDF) (TechRepublic)
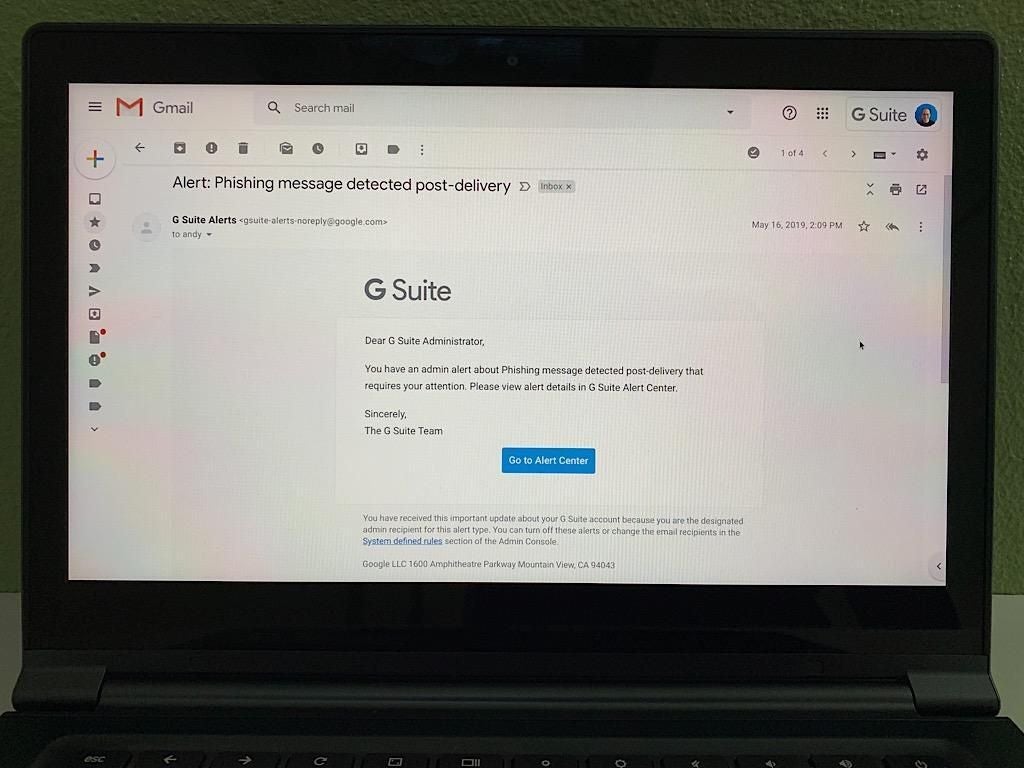
1. Check sender details
Expand the email sender details box to take a quick look at the sender details. A legitimate message should indicate that the email is sent from and signed by “google.com” with Standard TLS Encryption (Figure A).
Figure A
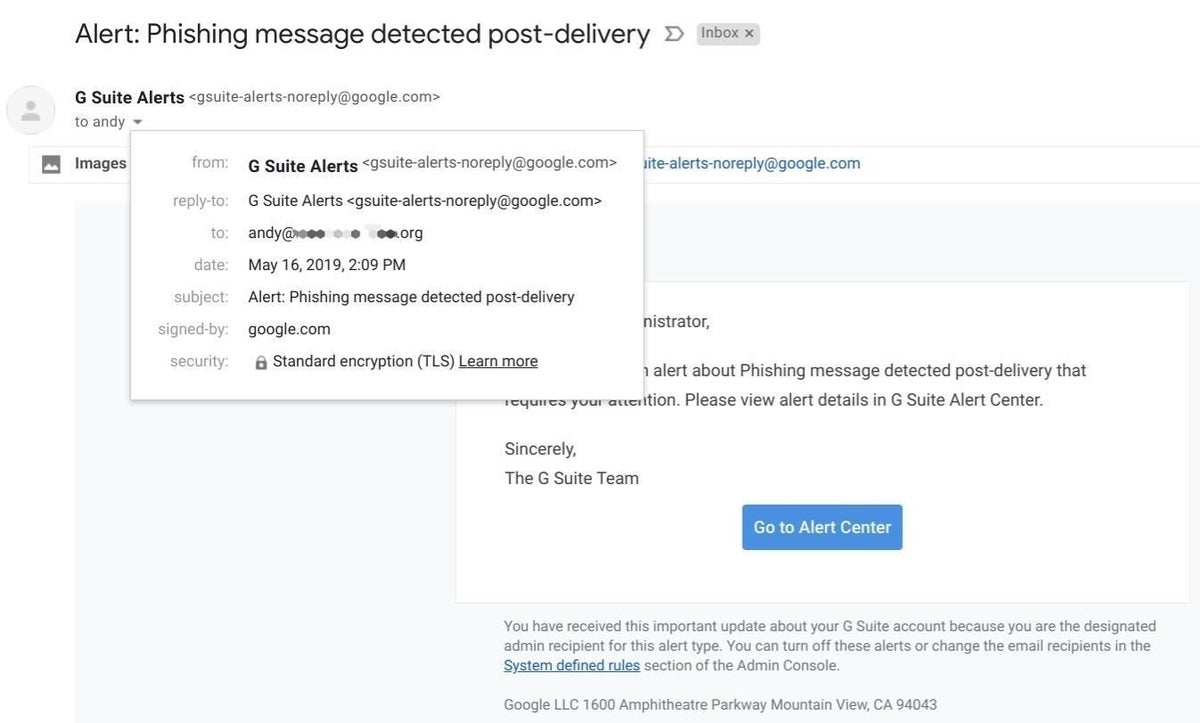
While the G Suite email about a phishing attempt includes a link with the text Go To Alert Center, you may be more secure if you don’t follow a link in an email regarding phishing–I advise my clients not to click the link.
2. Sign in to the G Suite Admin console
Type the address https://admin.google.com into your browser to go to the G Suite Admin console. Sign in with your G Suite administrator account credentials.
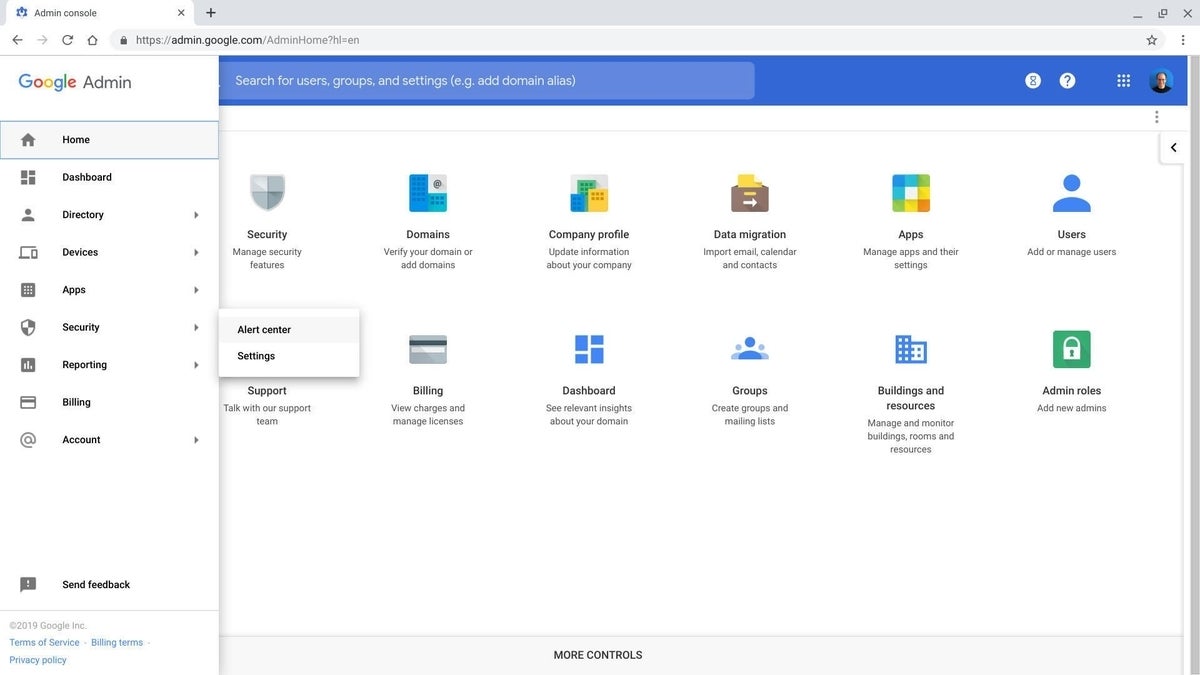
3. Access the Alert Center
View security alerts in the Alert Center, which you may access in at least two ways. First, select the three-horizontal line menu in the upper left corner of the Admin console, place the cursor over Security, and select Alert Center from the options that display (Figure B). Alternatively, once you’re signed in to the Admin console, you may also type https://admin.google.com/ac/ac to go directly to the Alert Center.
Figure B
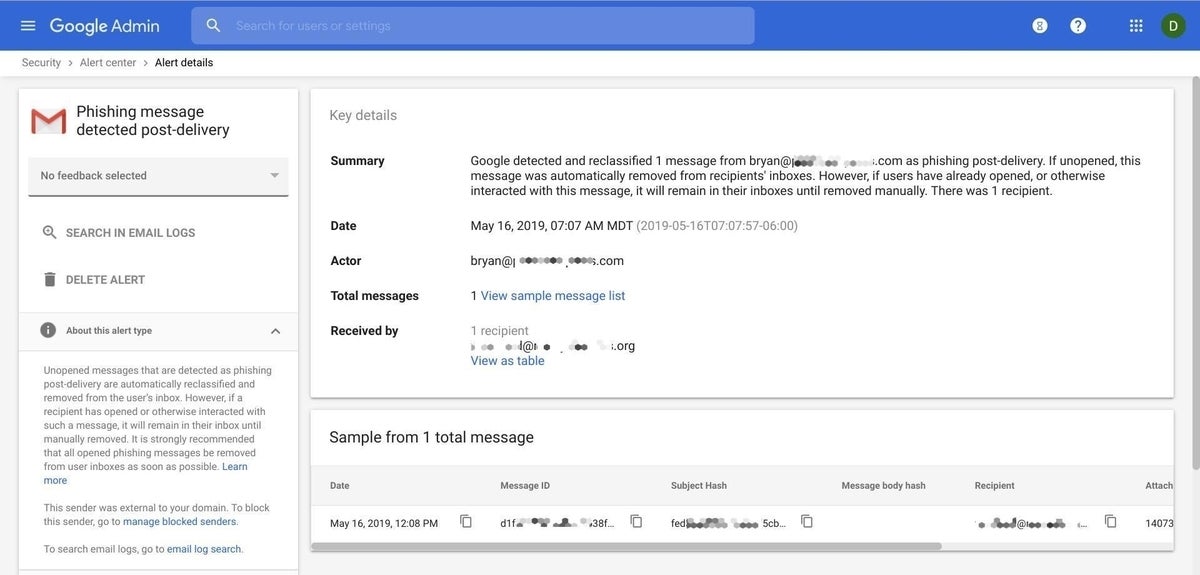
4. Review details of the phishing email
The Alert Center indicates the email address of the account to which the phishing email was delivered. The system also shows the email address of the purported sender, as well as the date and time of delivery (Figure C).
Figure C
5. Review account logins
If a person opens and follows a link in a phishing email, they may reveal information to the system and/or person that initiated the phishing.
To help ensure that account sign in details remain protected, look for account logins after the date the phishing email was received. While in the G Suite Admin console, go to Reports, then look for Audit and select Login (Figure D).
Figure D
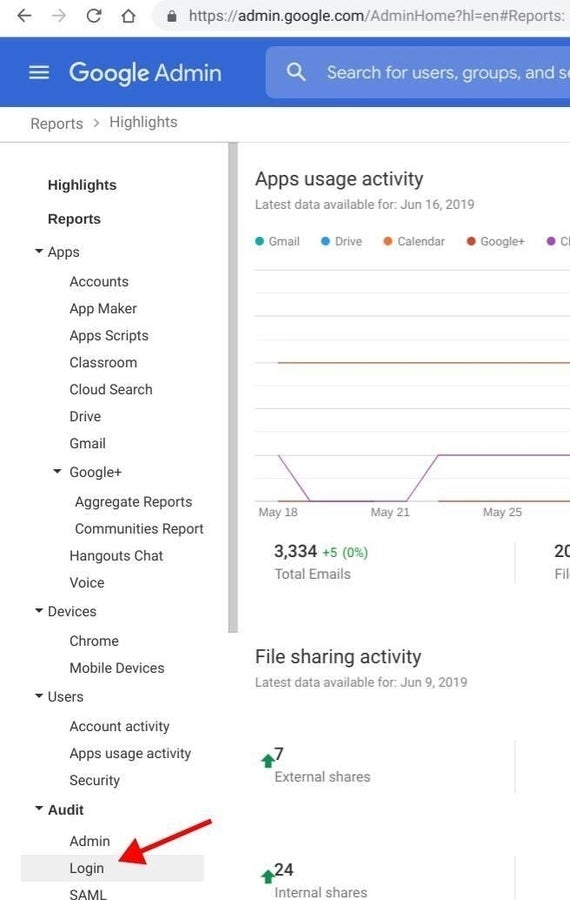
Type the email address of the person who received the phishing email in the User Name field. Then enter the date and hour that the phishing email was received in the From field in the Date And Time Range. Select Search to display the list of account logins by the phishing account (Figure E).
Figure E
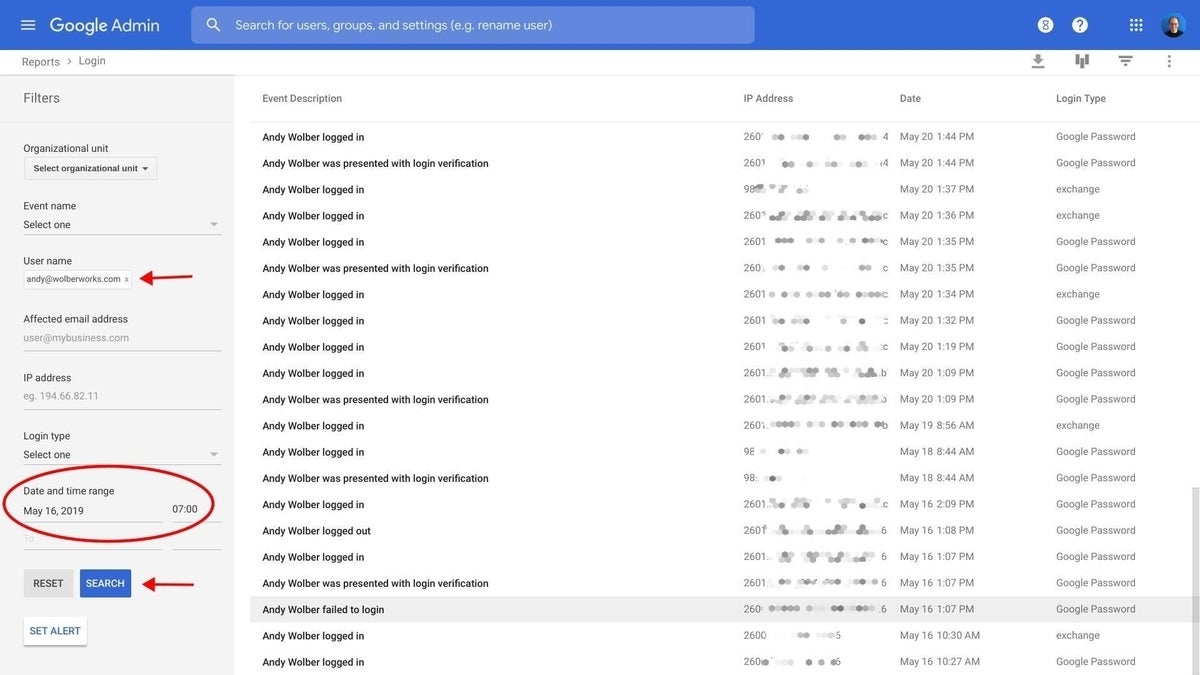
If you see signins from unusual IP addresses, you may want to reset the person’s password. You may also want to search Reports | Audit | Admin for additional administrative changes or activity for this account after the phishing email date.
6. Notify the recipient
In some cases, you may choose to notify the person who received the phishing email. You might also share a screenshot of the Alert Center information about the phishing email along with an email that lets the recipient know that Google identified a phishing email after it had been placed in the person’s email. If you’ve reset the person’s password, notify them of this event through your organization’s standard password change notification process.
If a person indicates they followed a link, or entered data in response to a phishing attempt, you may need to take additional steps to secure accounts and protect data. Google gives G Suite administrators several settings to configure that provide even stronger protection from phishing.]
Your process?
As a G Suite administrator, how often do you receive a notice that a phishing message has been removed post-delivery? Do you take action as described above, or do you follow a different process? Let me know how you handle this type of incident, either in the comments below or on Twitter (@awolber).

Image: iStockphoto/weerapatkiatdumrong