
Image: djedzura/ iStock
Ransomware attacks have increased seriously in the last two years, targeting every vertical of the corporate world. You might assume these cybercriminals are very skilled, since they are able to compromise a lot of companies; what if I told you they are maybe not as skilled as you might think, and that a lot of these groups simply buy the access to companies from other cybercriminals? Welcome to the world of initial access brokers.
What are initial access brokers?
Initial access brokers sell access to corporate networks to any person wanting to buy it. Initially, IABs were selling company access to cybercriminals with various interests: getting a foothold in a company to steal its intellectual property or corporate secrets (cyberespionage), finding accounting data allowing financial fraud or even just credit card numbers, adding corporate machines to some botnets, using the access to send spam, destroying data, etc. There are many cases for which buying access to a company can be interesting for a fraudster, but that was before the ransomware era.
SEE: Cybersecurity strategy 2021: Tactics, challenges and supply chain concerns (TechRepublic Premium)
Seeing the massive mediatization of ransomware cases, some cybercriminals decided to go for it and try on their own to make easy money this way – well, not so easy, since it requires technical skills to compromise a company and get a foothold on its network. This is where IABs come into play.
Ransomware groups saw an opportunity here to suddenly stop spending time on the initial compromise of companies and to focus on the internal deployment of their ransomware and sometimes the complete erasing of the companies’ backup data. The cost for access is negligible compared with the ransom that is demanded of the victims.
IAB activities became increasingly popular in the cybercriminal underground forums and marketplaces (Figure A).
Figure A
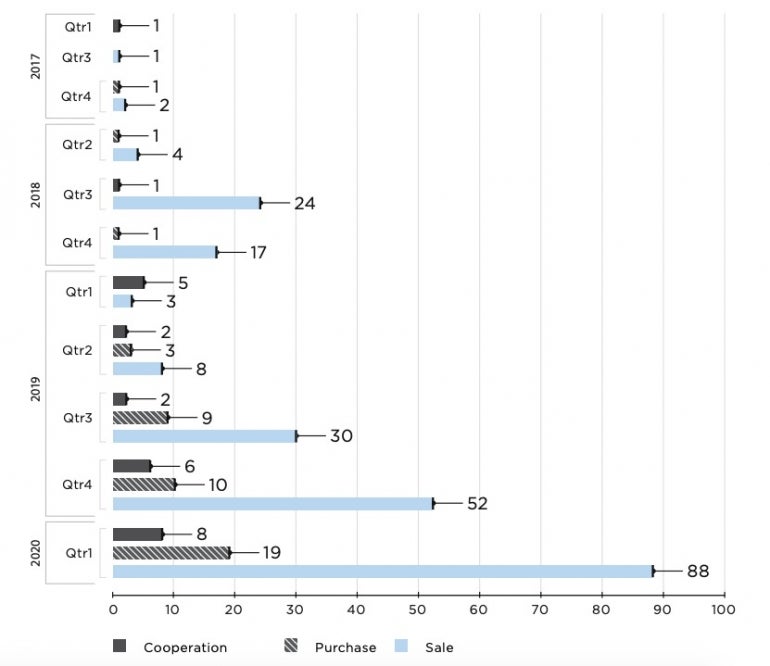
To sell the access in these marketplaces, the brokers always advertise using the same kind of information: the industry to which the company belongs, its number of employees, its revenue, the type of access and the price for it (Figure B).
Figure B
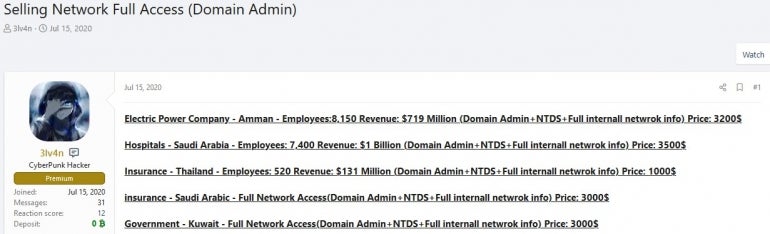
The price for accessing a corporate network roughly varies between $1,000 and $10,000. The IABs also generally provide the access exclusively to one customer, but it is not so rare that brokers with low reputations sell the same access to several different customers at the same time before disappearing.
What kind of access do IABs sell?
Active Directory credentials
The most valuable access an IAB can sell is a domain administrator access, with the ability to access the Active Directory of the company. That kind of access drastically reduces the amount of work for any ransomware group, because they immediately can use it to distribute malware all over the network.
Panels access
Access to different control panels that are accessible from the internet can be sold by IABs. Such panels generally provide access to web hosting content, often including payment solutions and therefore credit card details. The most popular of such panels is cPanel.
Web shell access
A web shell is a small piece of software that quietly lies on the architecture of a web server. It is generally hidden in a folder, and only the attacker who compromised the web server and put the web shell there knows how to access it. In addition, some web shells can have their access protected by a password set by the attacker. Some IABs set up web shells on compromised web servers and sell access to it.
RDP access
The most common access sold in underground forums is Remote Desktop Protocol access. This protocol is very popular among companies, especially for remote workers who can access corporate resources this way. All it needs is a login and password, and it is quite easy for an attacker to do massive scans for RDP servers all around the internet and try to brute force it.
VPN access
More and more companies have deployed virtual private networks to allow their remote employees to connect to the corporate network and work efficiently. The same as with RDP, if there is no two-factor authentication, it only takes a login and a password to get access to the corporate network.
Virtual machines access
IABs increasingly sell root access to VMware ESXi servers to ransomware gangs. DarkSide ransomware, for example, contains code that specifically targets those systems.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
RMM access
Remote Monitoring and Management is software designed to help IT professionals manage networks. They offer elevated permissions into several machines of the network, making it interesting data for IABs to sell.
How can I protect our business from IABs?
How can a company protect the assets that are at risk from initial access brokers? Follow these recommendations to reduce the risk.
VPN/RDP/RMM/control panels access
- Only use RDP and VPN gateways that support 2FA. Also only use control panels allowing 2FA. While it is still possible to hack those, it is complicated to sell such access since it needs manual work for every access. A cybercriminal who wants access to a company will certainly not use that solution and will try to get another.
- Enable Network Level Authentication for RDP access.
- Have a strong password management policy to avoid the brute-forcing of easy passwords.
- If possible, don’t allow remote connections for privileged accounts.
- Automatically lock out users with more than three or five unsuccessful login attempts and investigate those.
- Some panels have security plugins. It should always be activated and used.
Web shells
Monitor the web content from your web servers. Check for any new file appearing in a folder that should not be accessed by guests and users. Also, in case an attacker replaces a file by a web shell, check for any hash change of any of these files that would not result from an update.
Monitor underground forums
Some companies provide monitoring of the Dark Web and more largely of multiple cybercriminal forums and marketplaces. Subscribe to those to be alerted any time the company is mentioned by cybercriminals, IABs in particular. That way, if unfortunately, the network is already compromised, maybe the impact can still be limited by reacting fast to the threat.
Don’t forget general security good practices
- Keep your systems and software always up to date, and always deploy patches as soon as possible. This might prevent an initial compromise via a new vulnerability.
- Run full security audits on your network and computers, and correct everything that needs to be changed or updated.
- Use Intrusion Prevention Systems / Intrusion Detection Systems (IPS/IDS).
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

